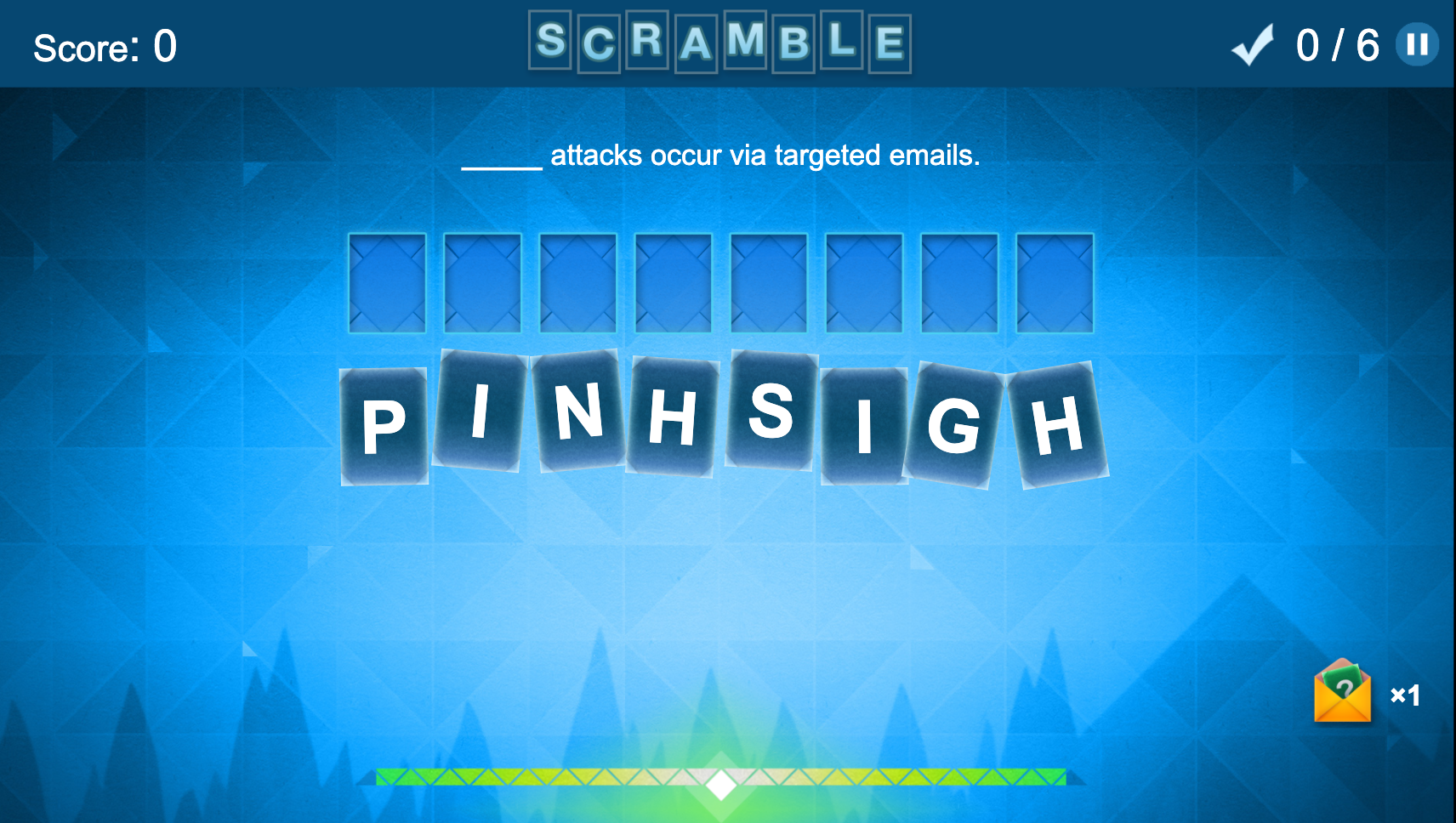
SECURITY
The Training Arcade® is used by some of the most highly regulated industries and corporations. As a result, we take security very seriously. Below is an overview of our protocols.
ACCESS CONTROL
TGA has defined processes for access management (e.g. provisioning accounts for users, limiting user access based on the principle of least privilege, terminating access, and periodic access certification). TGA access to client data is governed by our Privacy Policy. The Training Arcade® resides on AWS. We maintain strong password configuration requirements (high character count, include lowercase and uppercase alphabetic characters, numbers, and symbols). and require multi-factor authentication to further secure the environment.
Passwords expire at least every 90 days and are encrypted at rest and in transit, using industry-standard information security encryption algorithms. For customer data on The Training Arcade® a protocol is in place to prevent connectivity between two sets of data. Specifically, every customer has a unique subdomain and we have a software protocol in place to prevent connectivity to data stored under a subdomain to which a customer is not authorized access.
ASSET MANAGEMENT
For systems that have access to Client Data, a separation of duties process is in place for approving and implementing access with sponsorship and duration documented. Access to Client Data is limited to providing the service and in accordance with our Privacy Policy. Employees and contractors are assigned unique user accounts to access Client Data, systems, and/or applications. We maintain a Data Classification policy that includes security requirements based on the classification of the data. We do not maintain any physical assets or servers in our offices. All information is stored within Amazon Web Services EC2 instances and RDS databases.
BUSINESS CONTINUITY
We have a Business Continuity Plan (BCP) and a Disaster Recovery Plan (DRP). The plans are part of a broader context that include Security, IT, Personnel, and company operations. Specifically, the BCP & DRP cover handling both disruptions (environmental, electrical, civic disruption, etc.) and destruction (fire, flood, explosion, earth movement, etc.) at our physical locations and the AWS data centers we use to deliver services. The plans include information on backup infrastructure and procedures, chain of command and communications to employees and clients, and overall system recovery. The annual test of our BCP and DRP was completed March, 2018. All clients using The Training Arcade® are notified when there are scheduled or unexpected interruptions to the service.
COMPLIANCE
For more information on the topics below, please refer to our Privacy Policy. We do not store, transmit, process, or access Client Data, systems, and/or applications from outside the United States. There are individuals responsible for ensuring compliance with Privacy, Regulatory, Legal, and Security requirements.
CRYPTOGRAPHY
All non-public data is encrypted in transit using TLS and our databases are encrypted at rest. Client Data is encrypted in transit over public networks. Remote access connections into our network occur over an encrypted tunnel (e.g. VPN). Logins and data transfers are secured with encryption for cloud connections (e.g. HTTPS, SFTP, etc.). Wireless networks are required to be encrypted in accordance with industry standards.
HUMAN RESOURCES
We conduct background checks on employees in accordance with local, state, and federal laws. We expand this to third parties and contract workers on a case-by-case basis depending on the specific engagement. We expand the scope of the background check when the situation requires it (e.g. our work in
banking/financial institutions).
INFORMATION SECURITY
We manage risk via policies governing web security, application security, server/IT security, business continuity, disaster recovery, change control, The Training Arcade® privacy policy & terms of use, The Training Arcade® subscription agreement, and The Training Arcade® guidelines and restrictions. Collectively, we review these policies at least annually. All confidential information, otherwise known as PII (personal identifiable information), is restricted to TGA administrators only. This includes access, handling, and destruction of data. Admin access is reviewed and granted by TGA super Admin on a monthly basis and ad hoc as required. TGA employs a third-party security firm that conducts annual training to team members based on their role and relative access to data and confidential data. A small group of administrators receives additional training related to best practices and the evolving threat landscape. There is a process to identify, monitor, track, and remediate all identified risks and vulnerabilities on an ongoing basis.
INFORMATION SECURITY INCIDENT MANAGEMENT
We have an Incident Management Policy and an Incident Management Team assigned to respond to security incidents. TGA has support agents that operate during business days, during business hours (Monday through Friday 9:00 AM to 6:00 PM EST). TGA also employs team members who are on call 24/7 and are notified of system outages, security events, and other major alerts. If required for the scope of work with Enterprise Learning we can employ dedicated support staff to meet customer requirements.
OPERATIONS SECURITY
When an issue is identified, TGA personnel log it in our task management system and assign it to the appropriate technical personal with priority level, description, and requested due date. Technical staff accepts the ticket by marking it as in progress. Once resolved, the ticket is sent back to the reporter who provides a quality assurance function and closes the ticket when satisfied. All updates and changes are deployed in commits and merged into the staging or production instances for deployment when appropriate. Production deployments do not occur on Fridays or Holidays except in the case of emergencies and critical updates. Backups of systems and data are performed daily.
ORGANIZATION OF INFORMATION SECURITY
We have an Information Security Policy and an Information Security team with defined Privacy and Security roles and responsibilities. Our Information Security group maintain contacts with Information Security special interest groups, specialist security forums, and professional associations (i.e. ISACA, CSIRT, (ISC)2, etc.)
PHYSICAL & ENVIRONMENTAL SECURITY
TGA is a US-based company that does not store any client data on its premises. Client Data resides in a secure data center and AWS facilities maintain environmental controls.
SYSTEM ACQUISITION, DEVELOPMENT
Change Control: TGA employs a formal change control process. Changes are monitored throughout the implementation process to ensure success. The process is spearheaded/owned by the product owner, and managed via stand-ups, sprint cycles, and backlog. Appropriate segregation of duties is maintained between change approvals and change implementation. Approvals are obtained for Emergency changes. There are separate development, test, and production environments. We ensure that client production data is not used in development, staging, or testing / QA environments. We have a vulnerability management program that includes remediation of vulnerabilities identified in network and application security tests.